Statement Of Applicability ISO 27001 Template is a critical component in the ISO 27001 Information Security Management System (ISMS). It serves as an essential document that outlines which information security controls from ISO 27001 are applicable to an organization and how they are implemented. The SoA not only demonstrates compliance but also plays a crucial role in risk management, internal audits, and continuous improvement of the ISMS. This article will provide a detailed guide on the Statement of Applicability, its purpose, and a template to help organizations effectively create their own SoA.
What is the Statement of Applicability (SoA)?
The Statement of Applicability (SoA) is a formal document that lists the controls chosen from the ISO 27001 standard’s Annex A. It specifies which controls the organization has selected to implement, explains why these controls are necessary, and identifies any exclusions or deviations from the ISO 27001 controls. In essence, the SoA serves as a bridge between the security objectives of an organization and the practical measures put in place to achieve those objectives.
The purpose of the SoA is to:
- Clearly communicate which security controls are applied within the organization.
- Ensure that all controls are justified based on the results of a risk assessment.
- Provide evidence of compliance during audits and assessments.
- Help in decision-making and prioritization of resources for security measures.
Why is the Statement of Applicability Important?
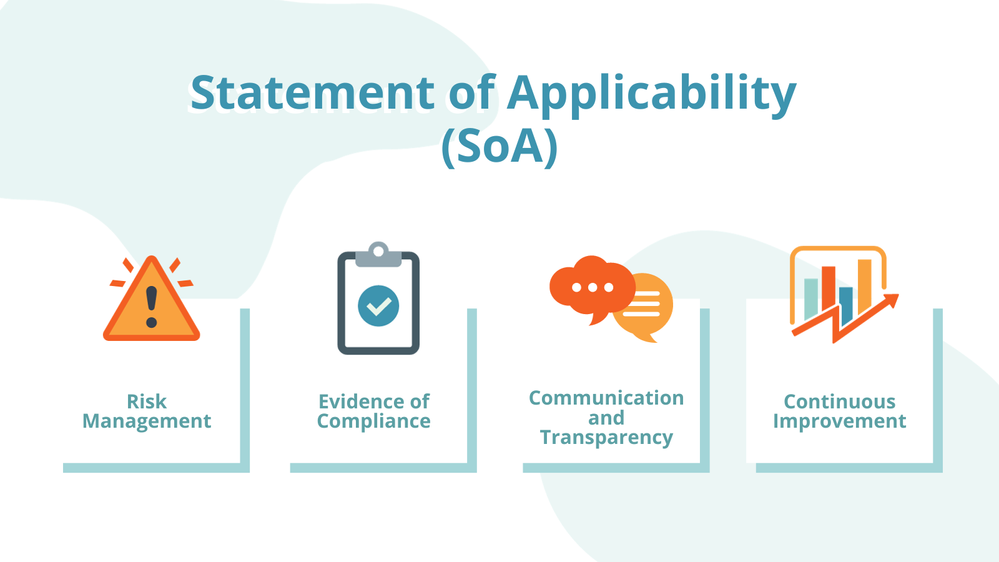
- Compliance and Audit Trail: The SoA is a key document for demonstrating compliance with ISO 27001. It ensures that all controls are implemented based on a systematic risk assessment and provides an audit trail that shows how decisions regarding the applicability of controls were made.
- Risk Management: It acts as a direct link to an organization’s risk management process. By identifying applicable controls, the SoA ensures that risks are appropriately mitigated, managed, and monitored.
- Internal and External Stakeholder Communication: The SoA facilitates transparency and communication regarding an organization’s information security practices with stakeholders, including employees, customers, and regulatory bodies.
- Continuous Improvement: By reviewing and updating the SoA regularly, organizations can ensure that their information security controls remain relevant and effective, addressing new risks as they arise.
Key Components of the Statement of Applicability
An effective SoA should cover the following key components:
- List of Controls: A list of the information security controls from Annex A of ISO 27001 that are applicable to the organization. These controls may include physical security, access control, incident response, and data protection measures, among others.
- Applicability: For each control, the SoA should indicate whether the control is applicable or not to the organization. If the control is not applicable, the organization must provide a rationale for the exclusion, such as the nature of the business, risk assessment outcomes, or the existing security measures.
- Implementation Status: The document should specify the implementation status of each control. This includes identifying whether the control is already implemented, partially implemented, or planned for future implementation.
- Control Justification: For each control that is deemed applicable, the SoA should provide a clear justification for why it is necessary based on the organization’s risk assessment and the identified threats and vulnerabilities.
- Owner of Control: The person or department responsible for the implementation and maintenance of each control should be identified. This ensures accountability and proper management of the security measures.
- Reference to Other Documents: If relevant, the SoA can reference other documents, such as policies, procedures, or guidelines that relate to the control. These documents will provide further context for the implementation of each security measure.
- Exclusions and Deviations: Any exclusions or deviations from the standard should be documented, along with the justification for why they were excluded or deviated from. This can be based on business needs, risk assessment findings, or external factors.
- Review and Update: The SoA should include a section for review and updates. Regular reviews ensure that the controls listed remain relevant and that the ISMS is continually improved.
How to Create Statement Of Applicability ISO 27001 Template
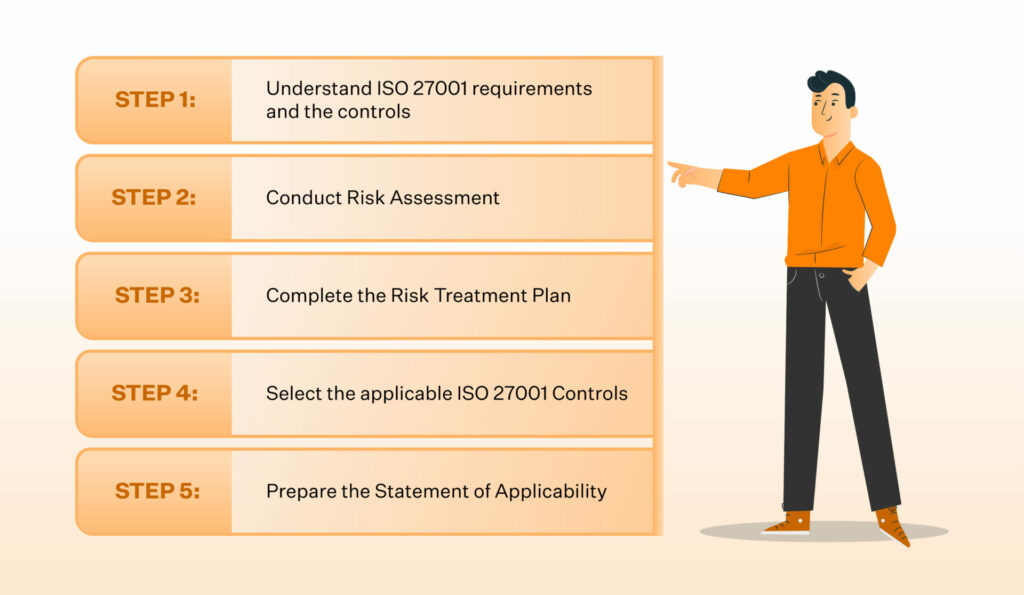
Creating an effective Statement of Applicability (SoA) requires a structured approach. The following steps outline the process:
Step 1: Conduct a Risk Assessment
Before you can determine which controls are necessary, you need to assess the risks to your organization’s information security. A thorough risk assessment will help identify the potential threats and vulnerabilities that need to be addressed. This step is critical as it forms the foundation for the controls you will select.
Step 2: Understand the ISO 27001 Controls
ISO 27001 Annex A contains a comprehensive list of information security controls. These controls are grouped into 14 categories, such as access control, cryptography, physical security, and business continuity management. You should familiarize yourself with these controls and consider each one in the context of your organization’s specific needs.
Step 3: Select the Applicable Controls
Based on your risk assessment, select the controls that are appropriate to mitigate the identified risks. Some controls may be immediately applicable, while others may require further consideration. Document the controls you have selected and ensure that you have a clear rationale for each choice.
Step 4: Justify Each Control
For each selected control, provide a justification for why it is needed. This should be based on the results of your risk assessment and any relevant business requirements. The justification could be related to protecting sensitive data, meeting regulatory requirements, or ensuring business continuity.
Step 5: Define Implementation Status
For each control, identify its implementation status. If the control is already in place, mark it as implemented. If the control is partially implemented, provide details on what has been done and what remains to be completed. For controls that are not yet implemented, outline the plans and timeline for implementation.
Step 6: Assign Ownership of Controls
Identify the individual or department responsible for implementing and maintaining each control. This ensures accountability and facilitates ongoing monitoring and improvements.
Step 7: Document Exclusions and Deviations
If any controls are excluded or deviated from, document the reasons for these decisions. This may include factors such as business needs, risk assessment findings, or existing measures that already address certain security concerns.
Step 8: Review and Update Regularly
The SoA is a living document that should be reviewed and updated regularly. As the threat landscape evolves and new risks emerge, it’s important to adjust your security controls accordingly. Regular reviews also ensure that your ISMS remains effective and aligned with business objectives.
| Control Number | Control Description | Applicability (Yes/No) | Justification | Implementation Status | Control Owner | Exclusions/Deviations |
|---|---|---|---|---|---|---|
| A.5.1.1 | Information security policy | Yes | To ensure that there is a defined and approved security policy. | Implemented | IT Security Team | |
| A.6.1.2 | Mobile device management | No | No mobile devices are used in the organization. | Not Applicable | N/A | Mobile devices are not used. |
| A.8.2.3 | Access control to information systems | Yes | Essential to protect against unauthorized access to information. | Implemented | HR Department | |
| A.9.2.1 | User registration and de-registration | Yes | Ensures that access rights are granted and revoked appropriately. | Partially Implemented | IT Department | Pending implementation in HR system |
Review and Update History:
- Be Clear and Transparent: Ensure that each control is clearly described and that justifications are backed by the results of your risk assessment.
- Involve Relevant Stakeholders: Include input from various departments to ensure that the controls reflect the actual needs of the organization.
- Ensure Regular Reviews: The SoA should be regularly reviewed to ensure that it stays aligned with the evolving information security landscape.
- Be Detailed but Concise: Provide enough detail to explain why controls are implemented but keep the document concise for easy reference.
- Use a Consistent Format: A structured and consistent format will make it easier to track and update the document.
Conclusion
Statement Of Applicability ISO 27001 Template is a cornerstone of the ISO 27001 certification process. It helps organizations ensure they have implemented the right security controls to mitigate risks, protect sensitive information, and comply with regulatory requirements. By following the steps outlined in this guide and utilizing the provided template, organizations can create a comprehensive and effective SoA that serves as a valuable reference for ongoing security efforts. Regular reviews and updates to the SoA will ensure that it continues to reflect the organization’s security needs and risk profile.



0 Comments