ISO 27001 Filetype PDF is a globally recognized standard for managing information security. Organizations that wish to secure their sensitive information and ensure data protection adopt ISO 27001, a comprehensive framework that covers risk management, security policies, processes, and controls. The standard focuses on the importance of establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS).
What is ISO 27001?
ISO 27001 is an international standard for Information Security Management Systems (ISMS), designed to help organizations establish, implement, operate, monitor, review, maintain, and improve the security of their information. The standard provides a systematic approach to managing sensitive company information, ensuring it remains secure by addressing the legal, physical, and technical controls required for managing risks to information security.
ISO 27001 sets the criteria for establishing an ISMS and identifies a range of specific information security controls that an organization can adopt. It helps organizations manage the confidentiality, integrity, and availability of their data. This certification proves that an organization has a strong information security management system in place and helps mitigate security risks.
Why ISO 27001 Certification Matters
ISO 27001 certification is an important achievement for any organization because it demonstrates a commitment to data protection, risk management, and regulatory compliance. It provides a competitive advantage, enhances customer trust, and helps organizations avoid the financial and reputational damages caused by data breaches or security incidents.
Key benefits of ISO 27001 certification include:
- Risk Reduction: It helps organizations identify potential threats to their information and implement measures to mitigate risks.
- Improved Business Reputation: Achieving certification can improve trust with clients, partners, and stakeholders by demonstrating the organization’s commitment to information security.
- Compliance: ISO 27001 helps organizations comply with various legal and regulatory requirements related to data security and privacy, such as GDPR or HIPAA.
- Competitive Advantage: It distinguishes the organization in the marketplace as a secure and trustworthy entity.
- Continual Improvement: The ISO 27001 standard promotes continuous improvement in information security management.
Key Components of ISO 27001

ISO 27001 provides a systematic approach to managing information security risks through a set of requirements. The standard is structured around the Plan-Do-Check-Act (PDCA) cycle and is composed of several key elements:
1. Leadership and Commitment
ISO 27001 requires top management to be actively involved in the development, implementation, and maintenance of the ISMS. Their commitment ensures that the ISMS aligns with organizational goals, receives the necessary resources, and is continuously supported.
2. Risk Assessment and Risk Treatment
A core aspect of ISO 27001 is identifying, assessing, and treating information security risks. This involves:
- Risk Assessment: Identifying and evaluating risks related to the confidentiality, integrity, and availability of information.
- Risk Treatment: Choosing the most appropriate control measures to mitigate or eliminate identified risks.
The organization must develop a Risk Treatment Plan that describes how identified risks will be managed and mitigated.
3. Information Security Policy
The standard requires organizations to establish an information security policy that sets the direction and scope for security management activities. This policy should:
- Outline the organization’s security objectives.
- Ensure alignment with business objectives.
- Define security responsibilities.
4. Security Controls
Annex A of ISO 27001 lists 114 controls divided into 14 categories. These controls cover various aspects of information security, such as:
- Access Control
- Cryptography
- Incident Management
- Business Continuity Management
- Physical and Environmental Security
Organizations must select controls based on the outcomes of their risk assessment and treatment plan. These controls help reduce the likelihood and impact of security threats.
5. Continual Improvement
ISO 27001 follows a continual improvement model. The ISMS must be regularly reviewed, updated, and improved based on performance monitoring, audits, and corrective actions.
Steps to Implement ISO 27001
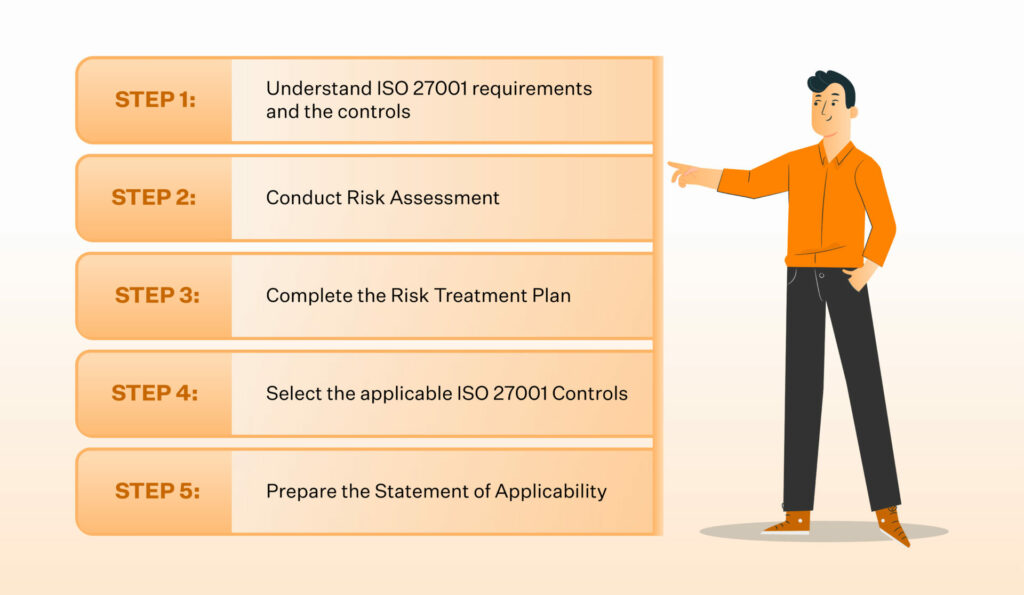
ISO 27001 implementation involves several steps. Below, we outline the key stages involved in setting up an ISMS and achieving certification.
Step 1: Establish ISMS Framework
- Define the Scope: Determine the boundaries of your ISMS and which information assets will be covered (e.g., departments, business units, or the entire organization).
- Appoint a Project Team: Designate individuals who will be responsible for implementing and managing the ISMS.
- Obtain Management Support: Secure support from senior leadership to ensure the necessary resources and commitment are provided.
Step 2: Conduct Risk Assessment
- Identify Information Assets: List all sensitive information, data, and systems that need protection.
- Assess Risks: Analyze potential threats and vulnerabilities to your information assets and assess the likelihood and impact of security breaches.
- Develop a Risk Treatment Plan: Based on the risk assessment, determine how to mitigate identified risks using appropriate controls.
Step 3: Develop Information Security Policies
- Create Security Policies: Develop clear policies that outline how the organization will manage information security and address risks.
- Define Objectives: Set measurable objectives for security performance and ensure that these align with the organization’s business goals.
Step 4: Implement Security Controls
- Put Security Controls in Place: Based on the risk treatment plan, implement appropriate technical, organizational, and physical controls to safeguard information.
- Employee Awareness and Training: Train employees on security policies, procedures, and best practices to ensure they understand their roles in protecting information.
Step 5: Monitor and Review ISMS
- Monitor Effectiveness: Regularly assess the performance of your ISMS to ensure it is working effectively. This includes conducting audits and monitoring key security metrics.
- Internal Audits: Carry out regular internal audits to assess compliance with ISO 27001 and identify any areas for improvement.
Step 6: Conduct Management Review
- Management Reviews: Senior management should regularly review the ISMS to ensure that it is meeting the objectives, identifying areas of improvement, and ensuring continual alignment with organizational goals.
Step 7: Achieve Certification
- Prepare for Certification: Once the ISMS is fully implemented, prepare for an audit by an accredited certification body.
- Stage 1 Audit: This initial audit focuses on reviewing your documentation and ensuring compliance with ISO 27001 requirements.
- Stage 2 Audit: This audit examines the effectiveness of the ISMS implementation, including interviews with staff and a review of evidence.
- Certification: If you pass the audit, the certification body will issue ISO 27001 certification.
Maintaining and Improving ISO 27001 Compliance
ISO 27001 requires ongoing maintenance and improvement of the ISMS. To ensure continued compliance, organizations must:
- Conduct Regular Audits: Regularly audit the ISMS to identify gaps, weaknesses, or non-conformities. Address these issues through corrective actions.
- Update Risk Assessments: As the organization’s environment and business processes change, continually reassess risks and update security controls accordingly.
- Engage Employees: Foster a culture of security awareness within the organization. Employees should be continually educated about emerging security threats and best practices.
- Review and Improve: Regularly review the effectiveness of your ISMS and make improvements based on performance metrics, audit findings, and feedback.
Conclusion
ISO 27001 is a comprehensive framework that helps organizations protect their sensitive information, manage risks, and comply with legal and regulatory requirements. By following the steps outlined in this article, organizations can establish an effective ISMS that not only protects their information but also demonstrates a commitment to security, instills trust among stakeholders, and provides a competitive advantage.



0 Comments