PDCA DO ISO 27001 is the globally recognized standard for establishing, implementing, maintaining, and improving an Information Security Management System (ISMS). One of the key principles in ISO 27001 is continuous improvement, which is achieved through the implementation of the Plan-Do-Check-Act (PDCA) cycle. This cyclical process helps organizations to develop, refine, and adapt their information security practices to effectively manage and mitigate risks over time.
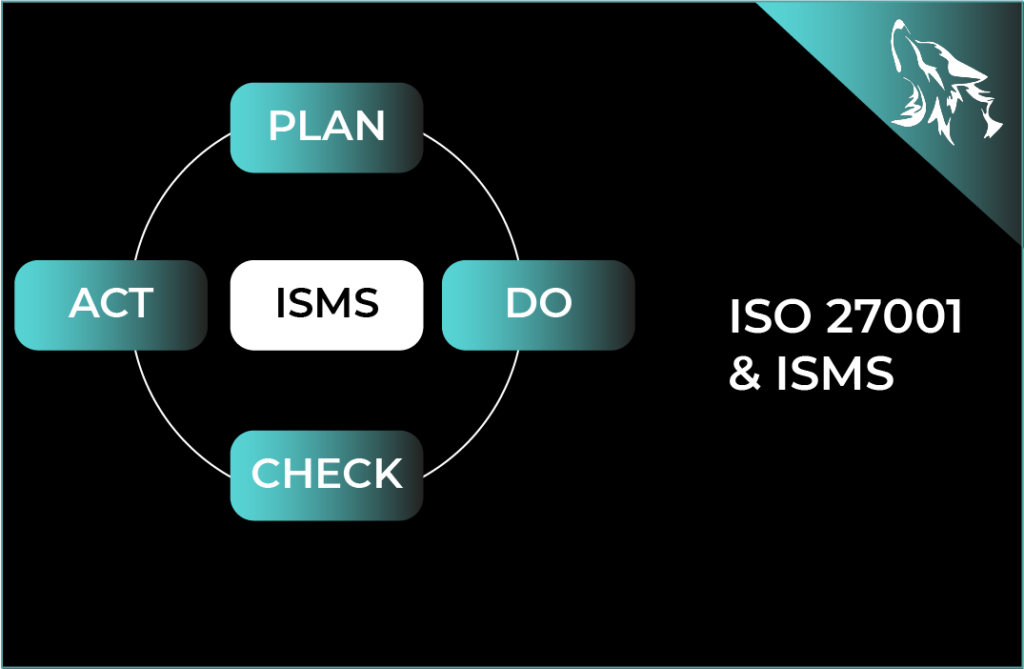
Understanding the PDCA Cycle
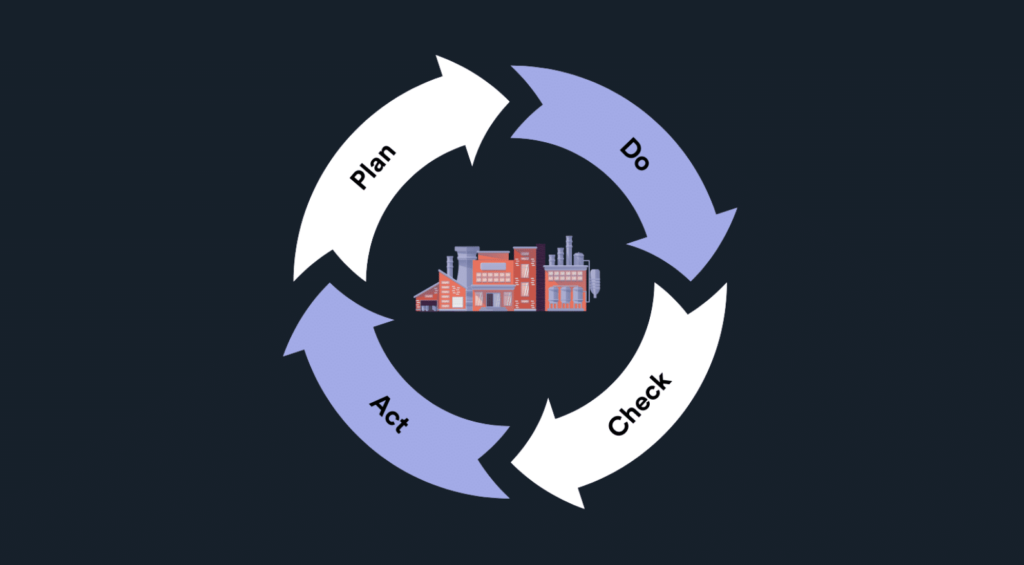
The PDCA cycle is a four-step approach designed to provide a structured framework for problem-solving, decision-making, and continuous improvement. Here’s a breakdown of each stage and how it relates to the implementation of an ISMS under ISO 27001:
1. Plan:
In this initial phase, the organization develops a clear and comprehensive strategy for its Information Security Management System. The planning stage involves several crucial activities:
- Risk Assessment and Treatment: Identify potential risks to information security, assess their likelihood and impact, and define risk treatment options.
- Establish Information Security Objectives: Set measurable goals aligned with the organization’s information security strategy.
- Define Policies, Procedures, and Controls: Develop the necessary policies and procedures to address identified risks, ensuring they comply with legal, regulatory, and contractual requirements.
- Assign Resources and Responsibilities: Define the roles and responsibilities of individuals involved in the ISMS, ensuring adequate resources are allocated for its implementation.
By defining these key elements in the planning phase, the organization sets the foundation for an effective ISMS and establishes a roadmap for the ongoing management of information security.
2. Do:
The “Do” phase involves the implementation of the plans and policies established during the planning stage. This is where the ISMS starts to take shape and operations are carried out according to the defined processes. Key actions include:
- Implementation of Information Security Controls: Put into practice the controls and measures that were designed to mitigate the identified risks.
- Training and Awareness: Ensure staff are trained on information security procedures, making them aware of their roles and responsibilities in safeguarding information.
- Execute Security Procedures: Carry out the security procedures, such as access controls, encryption, and incident response, to manage risks effectively.
At this stage, it is important to ensure the proper execution of all processes to meet the desired outcomes of the ISMS.
3. Check:
The “Check” phase focuses on monitoring, measuring, and evaluating the performance of the ISMS to ensure its effectiveness. This stage involves:
- Conducting Internal Audits: Regularly audit the ISMS to verify that it is being properly implemented and operating as intended.
- Monitoring Security Controls: Continuously assess the performance of security controls through monitoring tools, incident reports, and security assessments.
- Reviewing Compliance: Ensure that the ISMS complies with ISO 27001 and other applicable regulatory requirements.
- Identifying Non-Conformities: Look for gaps or weaknesses in the ISMS and identify areas where the system is not performing as expected.
The “Check” phase ensures that the organization is on track to meet its information security objectives and provides insights for areas that need improvement.
4. Act:
The final phase of the PDCA cycle is about taking corrective actions and improving the ISMS based on the findings from the “Check” phase. This phase involves:
- Corrective Actions: Address any identified non-conformities, deficiencies, or risks that were discovered in the monitoring process.
- Continual Improvement: Use the lessons learned to refine policies, procedures, and controls to improve the overall effectiveness of the ISMS.
- Management Review: Senior management should regularly review the results of the audits, monitoring, and corrective actions to ensure that the ISMS remains effective and aligned with the organization’s objectives.
By following the “Act” phase, organizations can refine their ISMS, making it more robust and resilient over time.
PDCA as a Foundation for ISO 27001 Implementation
The PDCA cycle provides a structured approach that ensures the ISMS is continually refined, adapting to new challenges, threats, and business requirements. Through repeated iterations of the PDCA cycle, organizations can:
- Maintain an effective information security posture.
- Respond to evolving risks in a proactive manner.
- Continuously improve the ISMS, aligning with both ISO 27001 standards and organizational goals.
Conclusion:
The PDCA cycle is a powerful tool for organizations looking to implement and maintain an effective ISMS in accordance with ISO 27001. By planning, executing, reviewing, and refining the information security management system, organizations can foster continuous improvement, mitigate risks, and ultimately protect sensitive information. The iterative nature of PDCA ensures that the ISMS remains dynamic and responsive to emerging security threats and regulatory changes, helping organizations maintain the highest levels of security and compliance over time.



0 Comments